Exfiltrated, Signed, Delivered – What Can Go Wrong When an Amazon Elastic Compute Cloud (EC2) Instance is Exposed to SSRF
New CNAPPgoat scenario makes experimentation easy by triggering calls to AWS service from an EC2 instance exposed to SSRF
Building Custom Scenarios with CNAPPgoat
You can now construct and import your own vulnerability scenarios into CNAPPgoat, enhancing your cloud security skills
The MGM Breach and the Role of IdP in Modern Cyber Attacks
A deep dive into the recent MGM breach and our insights into the actor behind the attack and possible mitigations.

What’s New with CNAPPgoat?
Read about the newest, expanded features in the Ermetic [now Tenable Cloud Security] open source vulnerable-by-design tool for enhancing your…

The Azure Metadata Protection You Didn’t Know Was There
Some Azure services have an additional, not widely known, protection mechanism against session token exfiltration

Stronger Together: Writing a New Chapter in Cloud Security
We’re excited to share that Tenable has announced intent to acquire Ermetic.
The Benefits of Cloud Entitlement Management
Cloud identities and entitlements pose grave challenges - learn about the benefits of CIEM solutions and KPIs for measuring them
The Next Step in the IMDSv1 Redemption Journey
Learn about AWS’s new open source library for enforcing IMDSv2 and Tenable Cloud Security’s new lab for trying it out
CNAPPgoat: The Multicloud Open-Source Tool for Deploying Vulnerable-by-Design Cloud Resources
All about CNAPPgoat, our open-source project designed to modularly provision vulnerable-by-design components in cloud environments.
Do I Need CNAPP If We’re Only Starting to Deploy to the Cloud?
It’s a leading question because no matter how new you are to the cloud you need CNAPP – find out…

Secure Your Cloud – Know the Difference between CSPM and KSPM
Conventional CSPM tools don’t sufficiently cover K8s clusters – dedicated tools are a must to address Kubernetes’s unique challenges

Sometimes What Sounds Benign Can Bite You: An Unexpected Implication of Lambda Privileges
Learn how an AWS service usage and permissions combination discovered by Ermetic [now Tenable Cloud Security] may increase risk upon…

The Default Toxic Combination of GCP Compute Engine Instances
By default, compute instances in GCP are prone to a toxic combination that you should be aware of, and can…
Shared Responsibility Model in the Cloud
CSPs have embraced a “shared responsibility model” to define the security responsibilities for different components of the architecture
Mastering the Art of Kubernetes Security
With Kubernetes’ explosive adoption by the development community comes an urgent need to secure K8s clusters and ensure their compliance…

Uncovering 3 Azure API Management Vulnerabilities – When Good APIs Go Bad
Learn how now-patched Azure API Management service vulnerabilities revealed by our research team enabled malicious actions
Cloud Workload Protection (CWP) Best Practice – Focus on Impact, Not Volume
How to do CWP right to prepare your organization and protect it from the next widespread vulnerability

Terraform Lab: Taking the New VPC Endpoint Condition Keys Out for a Spin
Our new open source Terraform project offers hands-on experience with VPC endpoints and demos AWS's new condition keys for securing…
Federating Kubernetes Workloads with Cloud Identities
Your K8s workloads legitimately need access to sensitive cloud resources – federated identities let you grant it easily and securely

Navigating Cloud Security: Why Segregating Environments from Dev to Production is so Important
Segregation in cloud environments is important for security - this post explores why and offers best practice tips for acting…

A New Incentive for Using AWS VPC Endpoints
If you haven’t been using VPC endpoints until now, AWS's two new condition keys should make you consider doing so

Managing Cloud Compliance and Security Posture with Cloud Compliance Tools
Why compliance and access security in the public cloud are so challenging – and how carefully chosen CSPM tools can…
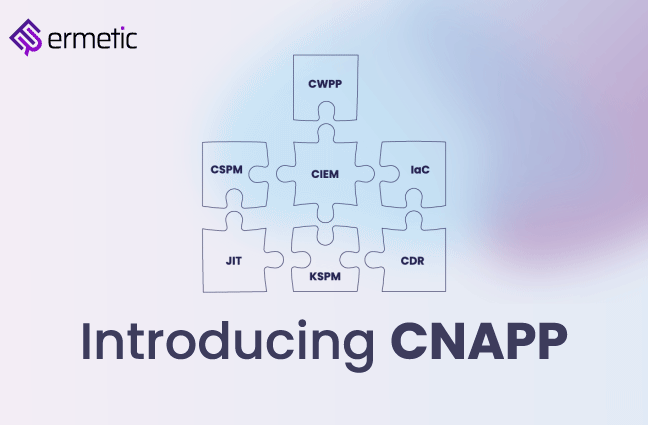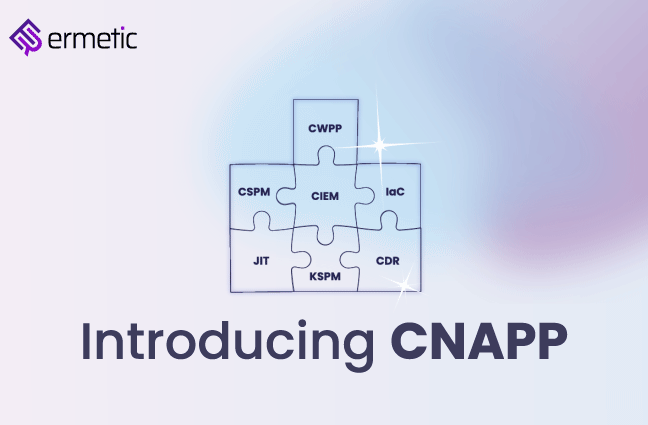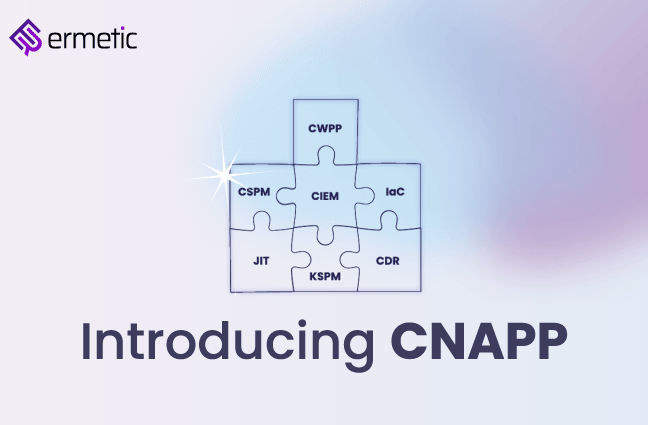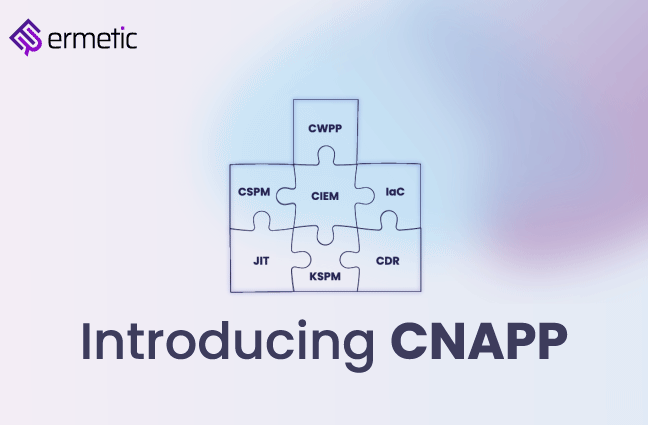
A Letter from the CEO
Introducing our Cloud-Native Application Protection Platform
Secure Your AWS EC2 Instance Metadata Service (IMDS)
Read this review of IMDS, an important AWS EC2 service component, to understand its two versions and improve your AWS…

Perceived Cloud Security vs. Reality: Test Yourself
Shun complacency -- your cloud security probably needs to be better than you, or your organization, perceive it to be

How to Implement CIEM – A Checklist
What differentiates a CIEM solution from other cloud security platforms, and how should a CIEM be used in an organization?…

How Attackers Can Exploit GCP’s Multicloud Workload Solution
A deep dive into the inner workings of GCP Workload Identity Federation, taking a look at risks and how to…
Fauda: When Hollywood and Cybersecurity Meet
The newest season of Fauda, now streaming on Netflix, is a real Hollywood meets Cybersecurity moment. Find out how realistic…
EmojiDeploy: Smile! Your Azure web service just got RCE’d ._.
The Ermetic [now Tenable Cloud Security] research team discovered a remote code execution vulnerability affecting Function Apps, App Service, Logic…
A Caveat for Azure VM Public IP Configuration
If you’re not familiar enough with the SKU attribute of the Azure public IP address, you may think you’re configuring…

How to Minimize Unintended Access and Achieve Least Privilege with Ermetic and AWS
Lior Zatlavi explains how to set up the platform in your environment and get maximum value

Why JIT Access is an Essential Part of Cloud Security
Automating JIT in the cloud is win-win for improving security and business productivity -- and cracks a nut that PAM…
Your Guide to IAM – and IAM Security in the Cloud
A look at how IAM works and how CIEM enhances IAM security in the cloud.

Usable Cloud Security – The Antidote to Cloud Complexity
Cloud security risk is ubiquitous yet manageable if you accept cloud complexity and seek solutions focused on usability and insights…

Sealing Off Your Cloud’s Blast Radius
Understand the challenges of securing your cloud and key best practices for minimizing your cloud’s blast radius

6 Cloud Security Tips For 3rd-Party Risk
It's critical to understand the security risk that third parties pose to your cloud infrastructure and how managing 3rd-party access…

How to Improve Your Incident Response in the Cloud
A look at the security best practices and mindset to adopt to better detect and recover from malicious activity in…

What You Should Know about the New OpenSSL Vulnerability
How to detect which OpenSSL version you’re running and if your organization is exposed to the critical OpenSSL vulnerabilities -…
IBM Cost of a Data Breach 2022 – Highlights for Cloud Security Professionals
Learn from the 2022 IBM report about the true cost of ransomware, compromised credentials and other breaches.

IAM Role Trust Update – What You Need to Know
When it comes to assuming roles, AWS is changing an aspect of how trust policy is evaluated; here is a…

Verizon’s 2022 Data Breach Report – Insights for Cloud Security Professionals
Wondering which cyber attack trends are putting your organization at risk? Learn about the leading threat vectors – and how…
Public Network Access to Azure Resources Is Too Easy to Configure
For some types of Microsoft Azure resources and subnets, it’s extremely easy to configure what is essentially public network access.…

Diving Deeply into IAM Policy Evaluation – Highlights from AWS re:Inforce IAM433
One of the most talked-about sessions at AWS re:Inforce, and my favorite, was IAM433, on AWS IAM’s internal evaluation mechanisms

Five Lessons Every Cybersecurity Team Can Learn from the Uber Incident
Upon hearing of a cyber security incident, alleged or factual, the most productive thing to do is learn what you…

IDSA Introduces CIEM Best Practices
The Identity Defined Security Alliance recently announced their list of Best Practices for Cloud Infrastructure Entitlement Management.

96% Could Have Prevented Their Identity Breach – IDSA
Identity-related breaches are on the rise but security and IAM pros are not idle. Learn from this survey how they…

Taking Notice of AWS IAM Roles Anywhere
IAM Roles Anywhere may be a pivotal moment for security — the new service lets you enrich the arsenal of…

DevSecOps: An Organizational Fix for Improving Cloud Security – Friction-free
By implementing the DevSecOps culture, tools and training, you’ll be on your way to more shift left security and less…
Test
Lorem ipsum dolor sit amet. Qui eaque doloribus ut ipsum dolores sit ducimus ratione. Nam laboriosam delectus vel itaque accusamus…

Facing the Shift-Left Security Conundrum. A True Story
Shift left security is hot – until it's not. Dynamic business requirements and cloud complexity pose major least privilege challenges.

3 Ways to Reduce the Risk from Misused AWS IAM User Access Keys
Used incorrectly, AWS IAM User Access Keys can pose high risk; the good news is that great alternatives, explored here,…

3 Types of Cyber Attackers: Which Organizations Do They Target?
Is an attacker interested in your organization? Probably. Deconstructing the PoV of cyber attackers is key to defending your turf.

Cloud Native and the Hype of Security
Through proper understanding and support, your organization can ensure it is secure while operating in the cloud and start taking…

What are CSPM solutions?
What are CSPM solutions and how can they help organizations stay compliant and avoid the security risks of misconfigurations? Answers…

Cloud and Data Security for Financial Services
Financial service organizations are adopting the cloud at a rapid pace. A robust solution for compliance and cloud security will…

AWS, Azure and GCP: The Ultimate IAM Comparison
AWS vs. Azure vs. GCP - how do these cloud providers compare when it comes to IAM? Read on to…

6 Tips for Successfully Securing Your AWS Environment
Top six actions and practices you can take to protect your AWS environment today.

Securing Your Cloud with Zero Trust and Least Privilege
Zero trust could be the solution for your modern security perils. Read on to discover what zero trust and least…

Identity Access Management in Google Cloud Platform (GCP IAM)
An introduction for anyone getting started with GCP or even experienced professionals who are looking for a structured overview.

Hidden Risk in the Default Roles of Google-Managed Service Accounts
Some Google-managed service accounts are binded by default to a role granting access to storage.objects.read. This hidden risk is (yet…

Verizon’s Data Breach Report – Insights for Cloud Security Professionals
Select highlights from Verizon’s recent Data Breach Investigations Report (DBIR) that may interest cloud security professionals – and suggested actions
How to Operationalize a Cloud Security Solution
How to successfully operationalize your cloud security solution in 4 easy steps – and why fast and effective operationalization matters

Lessons Learned in Cloud Security from Lapsus$ Surfacing
Cloud security practitioners can learn about the best practices that reduce the threat of cyber attacks from groups like Lapsus$.

Access Undenied on AWS
Introducing our new new open-source tool: Access Undenied on AWS. The tool parses AWS AccessDenied CloudTrail events, explains the reasons…

7 Cloud Security Trends That May Impact Your Cloud Security Planning
From leading CSPs to growing interest in multicloud, here’s what’s trending in measurable search traffic around cloud security - and…

The GCP Shared Responsibility Model: Everything You Need to Know
What the GCP Shared Responsibility Model is and how security teams can get started

3 Cloud IAM Security Questions You Must Be Able to Answer
It doesn’t matter if it’s AWS, GCP or Azure IAM, cloud deployment is redefining the work of IAM professionals

Cloud Identities and the Not So Long and Slightly Winding Road to Governance
A look at Forrester’s roadmap for the deployment and use of CIG to decrease the cloud threat surface and the…

How CSPM and CIEM may Solve your Cloud Compliance Challenges
With compliance essential to your organization, what strategy to take? Can you rely on a standard cloud security posture management…

Keep Your S3 Safe from CloudTrail Auditors
AWSCloudTrailReadOnlyAccess currently allows s3:GetObject for “*” and s3:ListAllMyBuckets – and reading CloudTrail logs may also give access to bucket object…

Wayward Sheriffs and Confused Deputies: Risks in GCP Third Party Access
Most GCP third-party vendors ask for permanent service account keys for access -- increasing credential leakage risk. Used correctly, short-lived…

How a Healthcare Provider Secures Its Cloud Infrastructure
Insights from a healthcare security executive on how automating risk mitigation and compliance boosted their cloud infrastructure security.

Cloud Native Application Protection Platform (CNAPP): An Evolving Approach to Cloud Security
A closer look at the newest Cloud Security category as defined by Gartner: Cloud Native Application Protection Platform (CNAPP).

Testing the Waters: First Impressions of CloudTrail Lake
Our first impressions of AWS's new managed audit and security lake that allows you to aggregate, immutably store, and query…

Tracking Adversaries in AWS using Anomaly Detection, Part 2
Going through the cyber “kill chain” with Pacu and using automated analysis to detect anomalous behavior

Tracking Adversaries in AWS using Anomaly Detection, Part 1
Minimizing the impact of a breach by identifying malicious actors’ anomalous behavior and taking action.

SEGA’s Saga of Nearly Compromised Credentials
A look at VPNO’s recent findings of publicly accessible S3 buckets on SEGA’s infrastructure and what we can learn from…

Top 7 Questions to Ask During a POC with a Cloud Security Vendor
A useful set of questions to help you get the most out of your upcoming POC -- and ensure that…

Protect Your AWS Environment Beyond Patching Log4j
The crucial strategic lessons overlooked by enterprises dealing with the recently reported Log4j vulnerability.

Top 6 Questions You Should Ask a Cloud Security Vendor
Choosing a cloud security platform and tools is not for the weak of heart – so much at stake! This…

Reaching for the Clouds with Our $70M Series B Financing
Ermetic is proud to have closed our Series B financing, enabling us to continue building the best cloud security platform…

How to Start Up Your Cloud Security
Startups may think they can postpone implementing a cloud security program but should in fact take early action - here’s…

Not Just Buckets: Are You Aware of ALL Your Public Resources?
A misconfiguration of resource based policies can inadvertently make resources public. Do you have such misconfigured policies present in your…

Useful Tips for Choosing a Cloud Security Vendor
A guide for what to take into account when starting to evaluate cloud security solutions. What to consider, how to…

How Smart Secrets Storage Can Help You Avoid Cloud Security Risks
The not-so-sensitive locations that may tempt you when storing sensitive information -- why to avoid them and how

The Top 24 Cloud Security Threats for Cyber Security Professionals
The complete checklist of threats and security gaps out to get your cloud

The Urgent Threat of Ransomware to S3 Buckets Due to Misconfigurations
Misconfigurations that can lead to S3 ransomware exposure and the mitigation tools you can leverage to prevent it

Five Strategies for Mitigating Your S3 Misconfiguration Ransomware Threat
Detailed steps for better ransomware protection of your AWS environment

CISO’s First 100 Days: A Guide to Getting Started
Everything you need to know about securing your cloud as a CISO.

Access Keys: An Unintended Backdoor-by-Design to Azure Storage Accounts Data
The importance of understanding the assignments of Azure resource roles when giving permissions.

The AWS Shared Responsibility Model: Everything You Need to Know
What the Shared Responsibility model means, its many challenges & how to protect your cloud infrastructure.

AWS Resource Provisioning with Attribute Based Access Control (ABAC) – What You Need To Know
What to pay attention to when using ABAC in order to avoid unnecessary security gaps.

Why Managing Security Posture and Entitlements from One Place Makes Sense
How a unified CSPM/CIEM platform can provide solutions to highly prioritized security risks, with minimal overhead.

The Importance of Identity and Access Management (IAM) in Cloud Infrastructure
How to manage human and service identities, and their entitlements, to secure your cloud infrastructure.

Repokid and Beyond: AWS Least Privilege, Gift-Wrapped
Travis McPeak explains why least privilege is so hard to achieve and how the automated approach works.

State of Cloud Security 2021: More Aware Yet Very Exposed
Dan Yachin digs into our State of Cloud Security 2021 Report and shares his insight.

Why Privileged Access Management (PAM) Fails Cloud Infrastructure…and What to do About it
PAM, its challenges for AWS, GCP and Azure environments - and CIEM as a solution.

TeamTNT Strikes Again: A Wake-Up Call to Start Securing Cloud Entitlements
Examining the news that TeamTNT is targeting 16 more applications, including Google Cloud.

AWS Condition Context Keys for Reducing Risk
A Least Privilege cheat sheet on using AWS global condition context keys to achieve least privilege.

Least Privilege Policy: Automated Analysis Trumps Native AWS Tools
AWS methods for granting & controlling access, plus native tools for detecting & repairing excessive permissions.

Best Practices for Securing Public Cloud Infrastructure
Bruce's suggestions for securing public cloud infrastructure, across industries.

Cloud Security: What’s Good for Fintech Is Good for… All Our Clients
Mohara shares how Ermetic keeps things secure and management-sane inside their cloud software development shop.

The ABCs of Azure Identity Governance Tools
The main Azure mechanisms for governing identities and providing access permissions.
AWS’s Access Analyzer Preview Access is Great — But Is It Enough?
Learn the ins and outs of the preview access capability in Access Analyzer.

Deconstructing Azure Access Management using RBAC
The basics of Azure RBAC -- the main mechanism in Azure for granting permissions to resources.

Keep Your IAM Users Close, Keep Your Third Parties Even Closer
An in-depth review on third-party access configuration and control with IAM permissions
Introducing the Ermetic Advisory Board: Gerhard Eschelbeck, Former CISO of Google
We recently announced the formation of the Ermetic Advisory Board which includes a who’s who of CISOs and cloud security experts from…

Auditing IAM PassRole: A Problematic Privilege Escalation Permission
How to determine which identities need iam:PassRole to help enforce “use it or lose it” least-privilege.

Cloud infrastructure is not immune from the SolarWinds Orion breach
Organizations exposed to the SolarWinds breach must identify exposed credentials and rotate them asap.

The AWS Managed Policies Trap
The “AWS Managed Policies Trap” and how to escape using automated analysis of environment configuration and activity logs.

Introducing the Ermetic Advisory Board: Elie AbenMoha of Publicis Groupe
Thoughts on cloud security from advisory board member Elie AbenMoha of Publicis Groupe

Who Holds the Keys to the Kingdom? (Part 2 of 2)
Part 2 takes a look at sensitive AWS Resources – secret strings and keys used in AWS.

Who Holds the Keys to the Kingdom? (Part 1 of 2)
Part 1 of a series takes a look at sensitive AWS Resources - secret strings and keys used in AWS.
Introducing the Ermetic Advisory Board: Adrian Ludwig of Atlassian
Adrian Ludwig of Atlassian shares his predictions and insights on public cloud security.

AWS Identity Federation and Least Privilege – Friends or Foes?
How to address the challenges in basic and advanced implementations of AWS federation.

The Three Ways of DevOps
Applying least privilege to cloud instances without adding bulk and delays to your pipeline.

Protect Applications and Data with Cloud Infrastructure Entitlements Management (CIEM)
Breaking down the hype around Cloud Infrastructure Entitlements Management (CIEM).

The Challenges of Securing Data Access in the Cloud, Part 4 (of 4)
Part 4 (of 4) - Sharing and Chaining Roles

The Challenges of Securing Data Access in the Cloud, Part 3 (of 4)
Part 3 - Looking beyond AWS IAM roles

The Challenges of Securing Data Access in the Cloud, Part 2 (of 4)
Part 2 (of 4): A closer look at IAM policies

The Challenges of Securing Data Access in the Cloud, Part 1 (of 4)
Part 1: Why is it so complicated to manage identities and entitlements in the cloud?

Why Information Security Must be as Adaptable as the Environment it Protects
Why information security must be more deeply integrated into everyday processes through intelligent automation.