The Unified Cloud Security Platform
From full asset discovery and deep risk analysis to runtime threat detection and compliance, Tenable’s Cloud Native Application Protection Platform simplifies even the most complex cloud security challenges. The unique identity-first approach dramatically reduces your cloud attack surface and enforces least privilege at scale.

The Tenable Edge
-
Remediate the Risks
that Matter MostReveal prioritized security gaps and facilitate immediate remediation.
-
Achieve Least Privilege and Zero Trust Access
Monitor permissions and continuously enforce least-privilege access.
-
Simplify
Complex IssuesTake control with powerful visualizations and risk-prioritized context.
-
Ramp up Security
from Dev to ProductionImprove security from dev to runtime without impacting app continuity or speed to market.
Secure your Cloud & Cloud Identities.
Tenable Cloud Security enables you to secure your cloud infrastructure from development to runtime. It continuously analyzes all your cloud resources to prioritize the risks, spot unknown threats and deliver actionable insights within hours. Tenable also addresses the #1 risk to your cloud infrastructure – identities – by detecting, prioritizing and remediating risky entitlements and misconfigurations at scale.
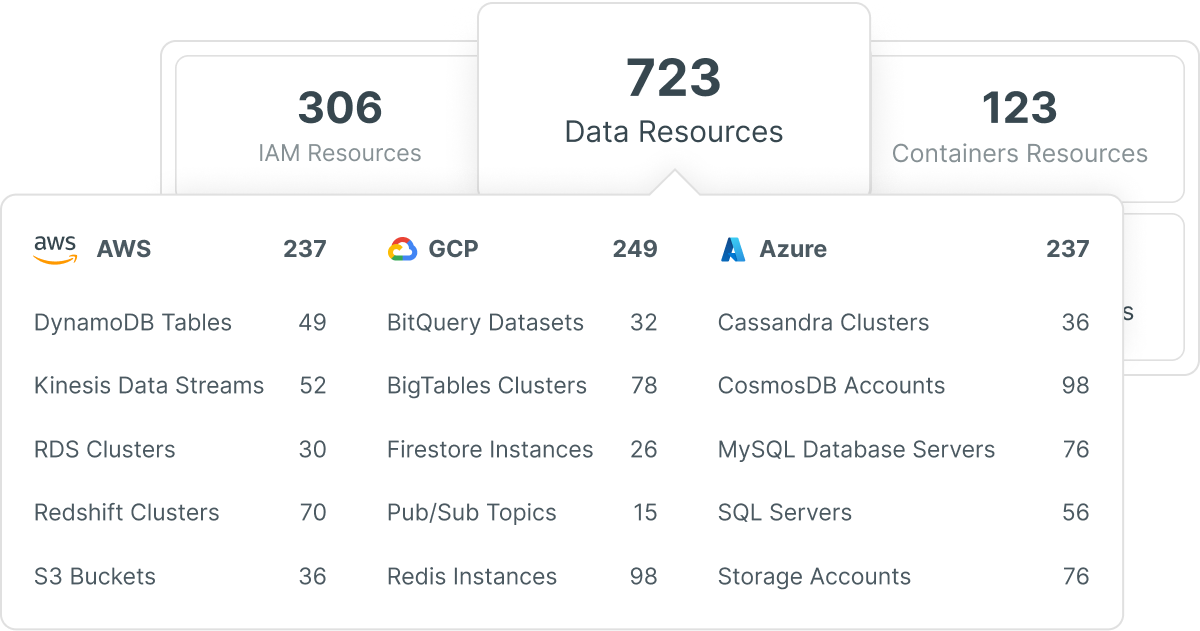
Multicloud Asset Management & Unified Visibility
Manage all resources including workloads, identities, data and network in one platform, with deep, centralized visibility. Investigate permissions, configurations and relationships to understand all cloud risks.


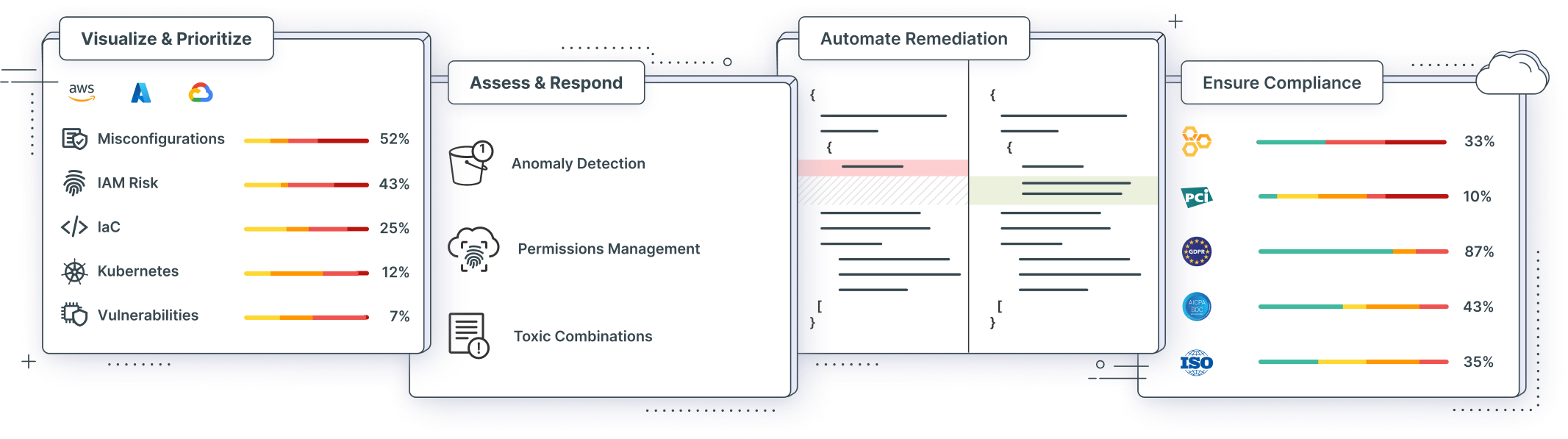
Full-Stack Risk Analysis & Prioritization
Assess and prioritize risk holistically across workloads, human and service identities, network and data resources, and configurations, to reveal and remediate security gaps.
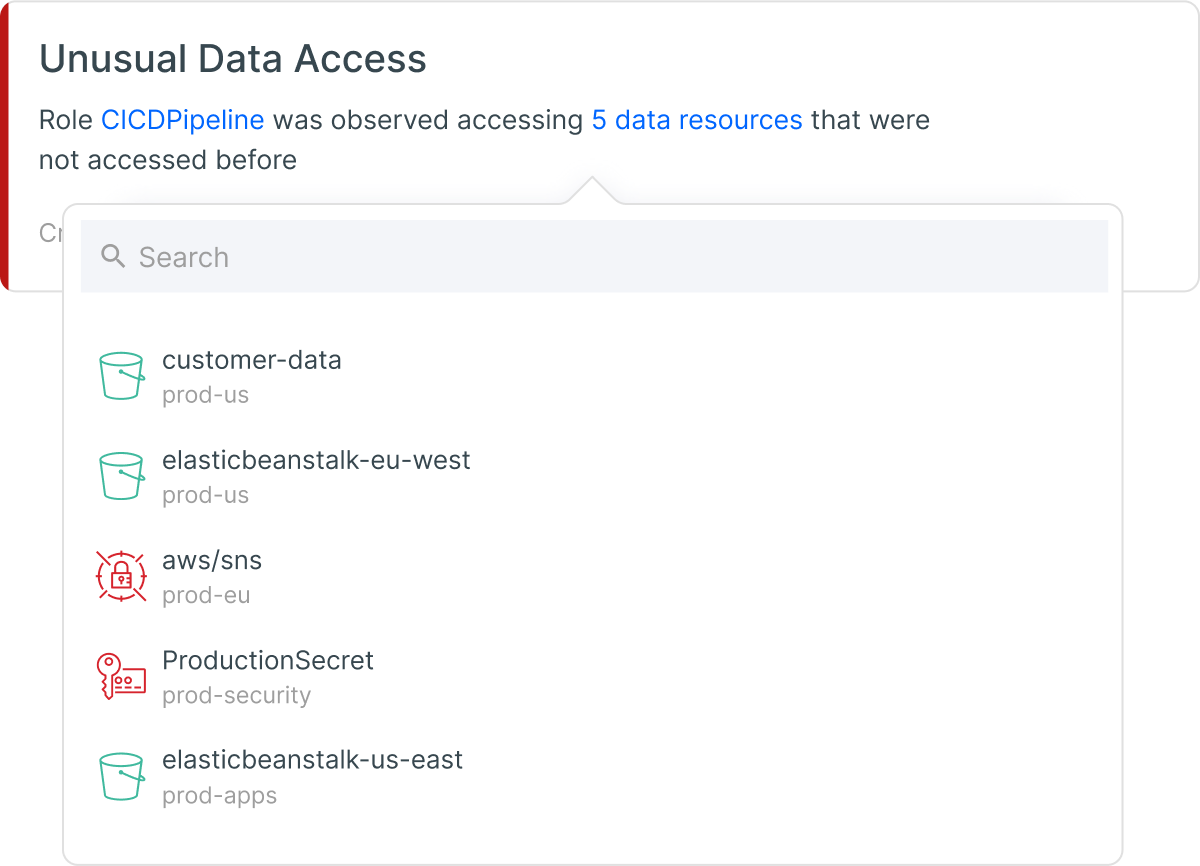
Threat Detection & Investigation
Automate threat detection with continuous behavioral analysis and anomaly detection based on built-in and custom policies. Accelerate investigation and remediation using enriched data sources and intuitive query tools.

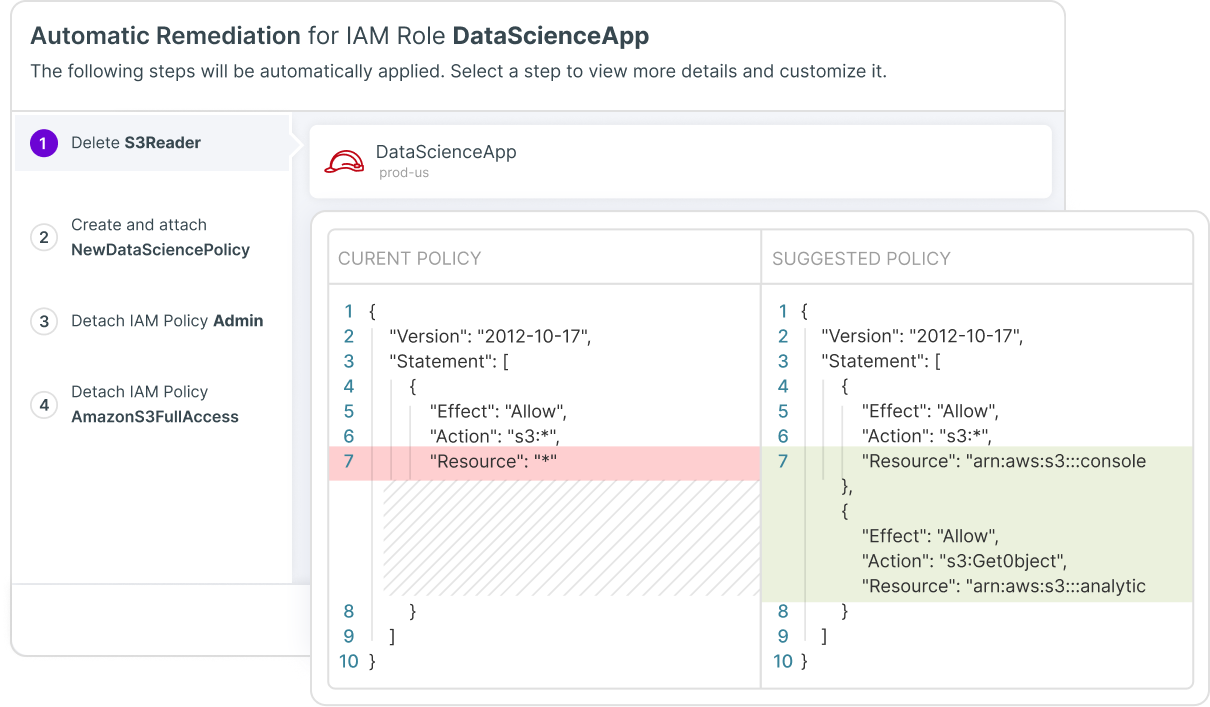

Automatic Remediation
Mitigate faulty configurations, policy violations and risky privileges. Automatically remediate with wizards, or send optimized policies and detailed remediation instructions through integration with cloud-native workflows, including collaboration and ticketing tools, CI/CD pipelines and IaC.
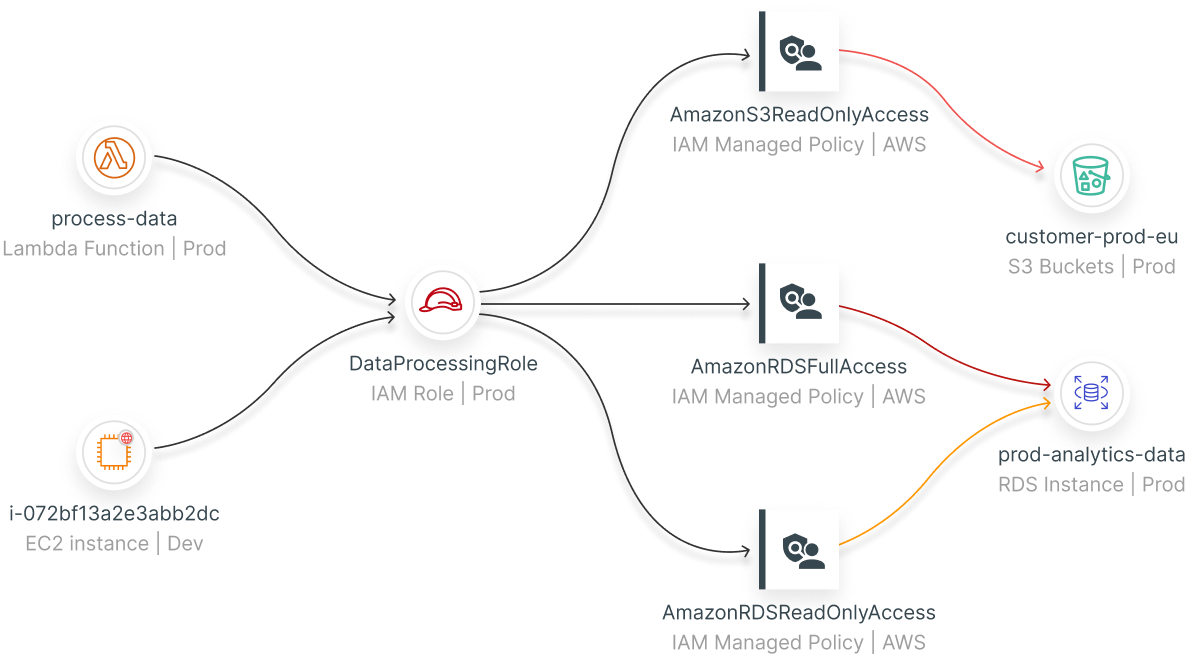
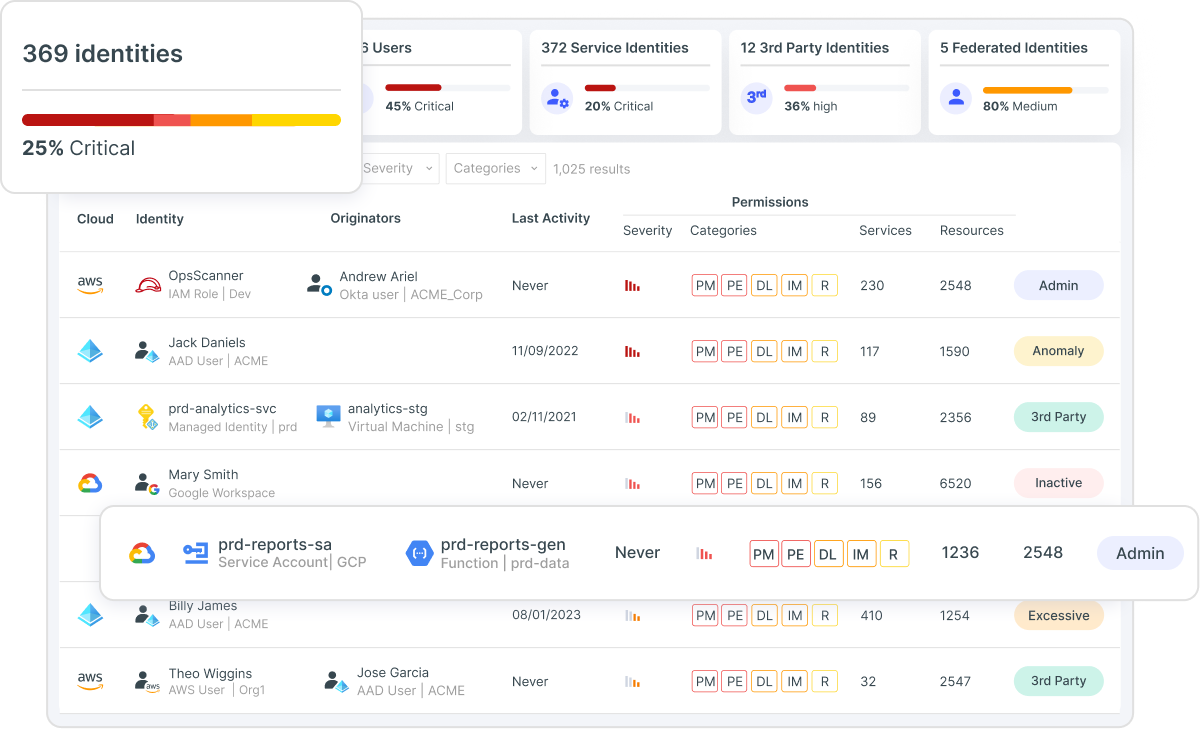
Secure Cloud Identities & Entitlements
Govern human and machine identities (CIEM) with full multicloud visibility into access entitlements and risk – including overprivileged and unused permissions, toxic combinations and privilege escalation. Enforce least privilege via automated right-sized policies and Just-in-Time access.

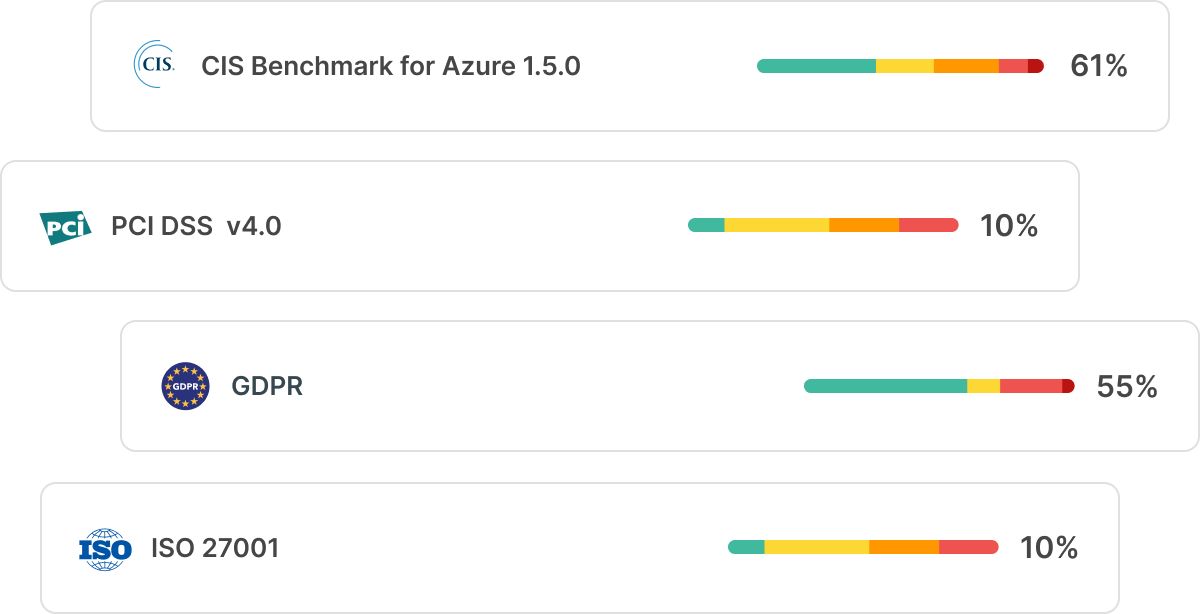

Gain & Maintain Compliance
Achieve compliance with frameworks such as CIS, AWS Well Architected, GDPR, SOC 2, NIST, PCI-DSS, HIPAA and ISO (CSPM). Define and enforce custom organizational policies for cloud configuration and IAM across clouds.
Explore More Tenable Cloud Security Capabilities
Implement shift-left security by scanning, detecting and fixing flaws in Infrastructure as Code. Reveal and remediate prioritized cloud risks in context and notify teams via integrations with ticketing and collaboration tools.
Learn moreGain full-stack visibility and accurate risk insights across network, configurations, identity, workloads and infrastructure as code. Democratize and accelerate security efforts across your teams, effectively reducing risk in even the most complex environments using guided remediation via wizards, workflows and CI/CD snippets.
Learn moreMonitor risk by continuously reviewing and assessing cloud environment settings and configurations. By mapping discovered risks against security standards and policies, organizations can attain and maintain compliance and regulation management across multicloud environments.
Learn moreAutomate risk analysis of Kubernetes clusters, including internal RBAC, detecting, prioritizing and alerting to vulnerabilities, misconfigurations and non-compliance. Integrate remediation in DevOps pipelines for fast response.
Learn moreSecure all identities (human and service) and resources in your multicloud environment. Enforce consistent least-privilege access across entitlements, policies and configuration settings.
Learn moreEfficiently scan workloads – including virtual machines, container images, runtime containers and serverless functions – for critical risks. Secure your cloud and maintain compliance by detecting exposed secrets, sensitive data, malware and misconfigurations.
Learn moreMinimize the cloud attack surface and avoid the risk caused by unwarranted long-standing privileges with granular Just-in-Time (JIT) access. Enforce least privilege in real-time by ensuring developers gain time-restricted elevated access to only the specific applications and systems required to perform needed tasks.
Learn more





