Tenable for Azure Cloud Security
Proactively managing security risks in Azure cloud infrastructure is a major challenge for enterprises looking to protect business-critical applications and data. The inherent gaps in coverage and visibility offered by disparate native Azure tools make it difficult to detect and prioritize cloud security risks.
Find out how Tenable’s holistic platform and identity-first approach drive actionable insights and streamline security operations for Azure and multi-cloud environments.

Andreas Pfau, Tribe Lead Business Solutions, BilfingerErmetic [now Tenable Cloud Security] is an independent tool giving us overall transparency and deep, unified insight into our cloud architecture across both Azure and AWS
Roadblocks to Protecting Your Azure Environment
The flexibility and agility of the cloud has enabled organizations to dramatically minimize time-to-value for their customers. However, the shift to cloud has made answering even basic security questions like “How many entitlements are excessive?” or “ Where do we need to improve compliance?” or “What are my top risks?” extremely difficult.
Existing solutions, including cloud-native tools, offer little relief. Teams often leverage a combination of tools to get the job done, but switching between multiple solutions to assess, investigate and remediate cloud security risks is no longer a viable option.
Cloud demands a different approach to security. Tenable Cloud Security dives deep to find the risks within your Azure or multi-cloud environments and offers step-by-step remediation – all while making even the most complex problems simple.
Complete Cloud Security for Microsoft Azure
Tenable Cloud Security is a comprehensive, identity-first Cloud Native Application Protection Platform (CNAPP) for Azure. The agentless solution unifies and automates asset discovery, risk analysis, runtime threat detection and compliance — across cloud infrastructure, workloads, identities and data. It identifies, prioritizes and remediates security and compliance flaws with pinpoint accuracy.
Tenable helps you shift left by hardening your Azure environment as part of the CI/CD pipeline. The platform democratizes security across devops, security and IAM teams.


Gain Continuous Cloud Security Posture Management (CSPM)
Simplify cloud compliance through a single platform that continuously scans configurations and resources across clouds, identifies violations and automates remediation. With Tenable’s intelligent CSPM, analyze configuration data and cloud assets against industry best practices, compliance frameworks and custom policies.
Meet Azure-specific data privacy mandates, security best practices and other industry benchmarks using built-in compliance templates or custom policies tailored to match your organization’s needs to ensure that your Azure environment is truly secure.
- Get a continuously updated picture of your cloud inventory and activity
- Prioritize risks and auto remediate based on business impact
- Demonstrate your ability to meet key data privacy mandates including PCI-DSS, GDPR, HIPAA and many more.
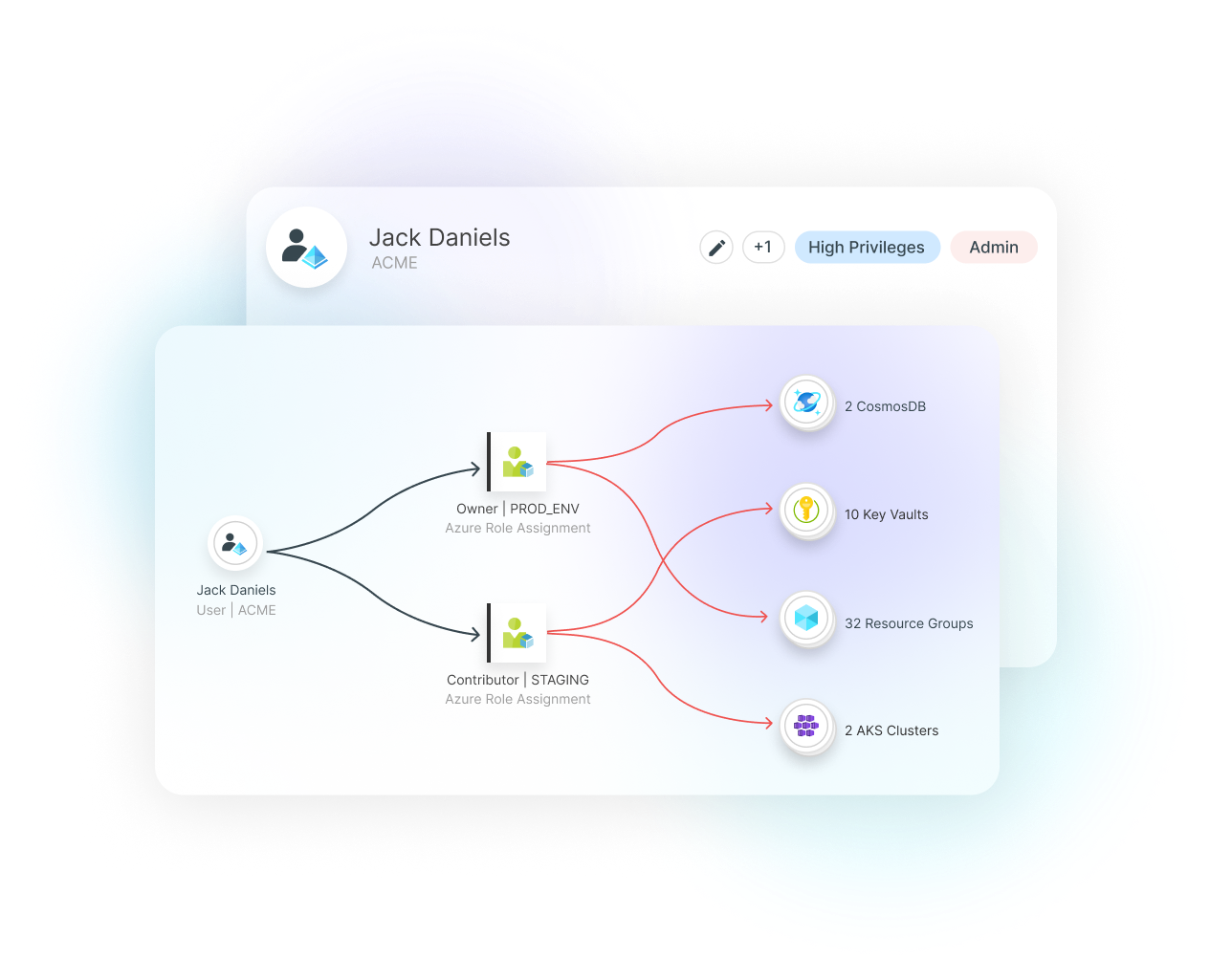
Secure Your Cloud Identities and Entitlements (CIEM)
Get equipped with actionable visibility, uncovering all identities and access paths across all Azure subscriptions and data stores. Tenable Cloud Security provides full stack risk analysis across identities and entitlements, network and cloud configurations — identifying toxic combinations, prioritizing and remediating risk with high accuracy.
Manage Azure IAM risks and enforce least privilege access and zero trust by finding, auditing and removing excess permissions.
- Visibility into excessive permissions, toxic scenarios, network exposure and more
- Get recommendations for assigning identities with Roles based on actual usage data
- Detect and investigate suspicious behavior in real-time
Enable Shift-left with Infrastructure as Code Scanning (IaC)
Developers and DevOps teams leverage Tenable Cloud Security to avoid errors, align with security policies and best practices, and harden Azure infrastructure as part of the CI/CD pipeline. The platform scans IaC for misconfigurations and risks in native development tools including Jenkins, BitBucket, CircleCI, GitHub and GitLab.
- Identify misconfigurations and compliance violations in code
- Automatically remediate by integrating fixes in existing workflows, ticketing systems and source code repositories
- Shift left to empower developers to remove configuration flaws prior to production
Agentless Vulnerability Scanning & Workload Protection (CWP)
Tenable takes an agentless approach to scan and detect critical workload risks. Its unified protection provides teams with a centralized, single point of visibility and control across all their Azure and multicloud environments.
By combining insights on vulnerabilities, exposed secrets / sensitive data, malware and misconfigurations, security and DevSecOps teams can reveal and effectively assess the full severity of a workload vulnerability.
- Gain deep visibility and context into cloud workload risk with intelligence gathered across virtual machines, serverless functions, container images and Kubernetes clusters
- Correlate vulnerabilities across OS packages, applications and libraries with additional workload characteristics to prioritize remediation efforts
Tenable Cloud Infrastructure Entitlements Management
-
Get Deep, Multicloud Visibility
Learn MoreManage all identities and resources in one platform. Investigate permissions, configurations and relationships
-
Understand the Attack Surface
Learn MoreAssess & prioritize risk across human and service identities, network configuration, data and compute resources
-
Automate Remediation
Learn MoreMitigate risky privileges and faulty configurations through integration with ticketing, CI/CD pipelines, and IaC
-
Enforce Policies and Shift Left
Learn MoreDefine and enforce automated guardrails for access permissions and resource configuration, from dev to production.
-
Detect Anomalies
Learn MoreDetect suspicious behavior and configuration changes with continuous behavioral analysis and alerts
-
Comply with Standards
Learn MoreAudit inventory and ensure compliance with CIS, GDPR, SOC2, NIST, PCI DSS, HIPAA, ISO and more
Featured Content for Microsoft Azure

Access Keys: An Unintended Backdoor-by-Design to Azure Storage Accounts Data
The importance of understanding the assignments of Azure resource roles when giving permissions.

[On-Demand] Eliminate Azure IAM Risks: How to Leverage Native Azure Tools and Automation to Pursue Least Privilege
Using access permissions analysis, RBAC and native tools in Azure toward least privilege.

The ABCs of Azure Identity Governance Tools
The main Azure mechanisms for governing identities and providing access permissions.



