How CSPM and CIEM may Solve your Cloud Compliance Challenges
With compliance essential to your organization, what strategy to take? Can you rely on a standard cloud security posture management tool – or do you need more?

When it comes to cloud compliance, check your mindset. If you think, as many do, that there’s a kind of silver bullet for addressing compliance – that it’s something you can take care of like an event and not deal with every day, think again. The complicated technology of cloud infrastructure, the unique cloud environment of every organization and people involved, and the dynamic nature of cybersecurity compliance defy a clear-cut solution to its implementation.
In this post, based on a recent webinar, we discuss the obscure yet very important topic of compliance and its impact on securing your cloud. We’ll cover several standards, why compliance needs to matter to you (but maybe not in the way you think) and optimal ways to meet the challenges of monitoring and improving compliance.
What is Cloud Compliance – and Who Is Responsible for It?
Let’s start by defining what compliance means in the cloud. Cloud compliance refers to the many regulations and best practice principles that organizations must follow for systems they deliver through the cloud. While cloud providers practice compliance for their products, cloud customers themselves must take their own compliance actions to meet the required guidelines.
By addressing compliance, organizations can monitor, assess, audit and mitigate their cloud risks, and increase governance. Cloud compliance is usually the direct responsibility of DevOps or DevSecOps, but pertains to security and IT teams, as well as CIOs, CTOs and CISOs.
Why Do Organizations Need to Get Cloud Compliant?
Organizations typically have three compelling motivations to comply with cloud regulations:
- Legal - The law requires following certain guidelines to avoid being sanctioned.
- Business - Compliance can provide a competitive advantage – or, in some cases, is even a minimal requirement. Either way, organizations often market their compliance adherence to prospects and customers, and use it to boost their reputation.
- Best practices - Compliance provides the foundation for the company’s security strategy. Rather than reinvent the wheel, the company uses its compliance needs as a starting point for implementing security and privacy practices.
Getting Familiar with Compliance Standards and Benchmarks
Regulatory standards and benchmarks abound: by industry, geographical region, country and more. Many, of course, are global; here are the most common:
- GDPR - Data protection, security and compliance for the EU
- HIPAA - Security and privacy protection of health information
- PCI DSS - Security controls to reduce credit card fraud
- ISO 27001 - Information security management
- SOC 2 - Customer data management
- Center for Internet Security (CIS) - Benchmarks for secure configuration of target systems
- NIST - A strict security framework for federal agencies and programs
- Cloud provider benchmarks - For building secure and resilient cloud infrastructure, such as AWS Well Architected and Azure best practices for IaaS workloads

Cloud Compliance Challenges: Not As Easy as It Seems
Despite appearing seemingly straightforward, achieving compliance in the cloud is not like filling out a few forms and being done with it. While some regulatory standards and best practices are very specific in their instructions, many others are much more abstract. An abstract standard could guide you to accomplish a certain goal without explaining how to do it. In such cases, it’s anyone’s guess as to the methods and tools that need to be implemented to accomplish it and what to do to ensure the achieved compliance lasts a long time (continuous compliance).
The reason some standards are so abstract is that security is not a one-size-fits-all practice. Cloud environments are multidimensional and dynamic; vulnerabilities keep evolving. Also, organizations have different use cases depending on their industry. A list of specific instructions could never cover everyone’s security bases.
As a result, security teams need to follow compliance practices to the best they can. Doing so calls for putting certain security controls in place. In many ways, compliance regulations are a starting point, not the finish line.
Compliance Challenge Spotlight: Least Privilege
Let’s see how this challenge plays out when attempting to achieve a popular security principle: least privilege. Quick reminder: Least privilege means setting up permissions so that an identity has only the access it needs to perform its business function – that is, permissions to perform an exact set of actions on an exact set of resources. Least privilege access is a coveted goal that every security practitioner wants to achieve.
In AWS, for example, permissions are assigned through policies. A policy document, for example, will list the actions that can be performed on specific resources. Resources can be designated with wildcards. Since policies are written in JSON and can be filled in freely, one can easily and unintentionally give an entity access to a wide range of resources.
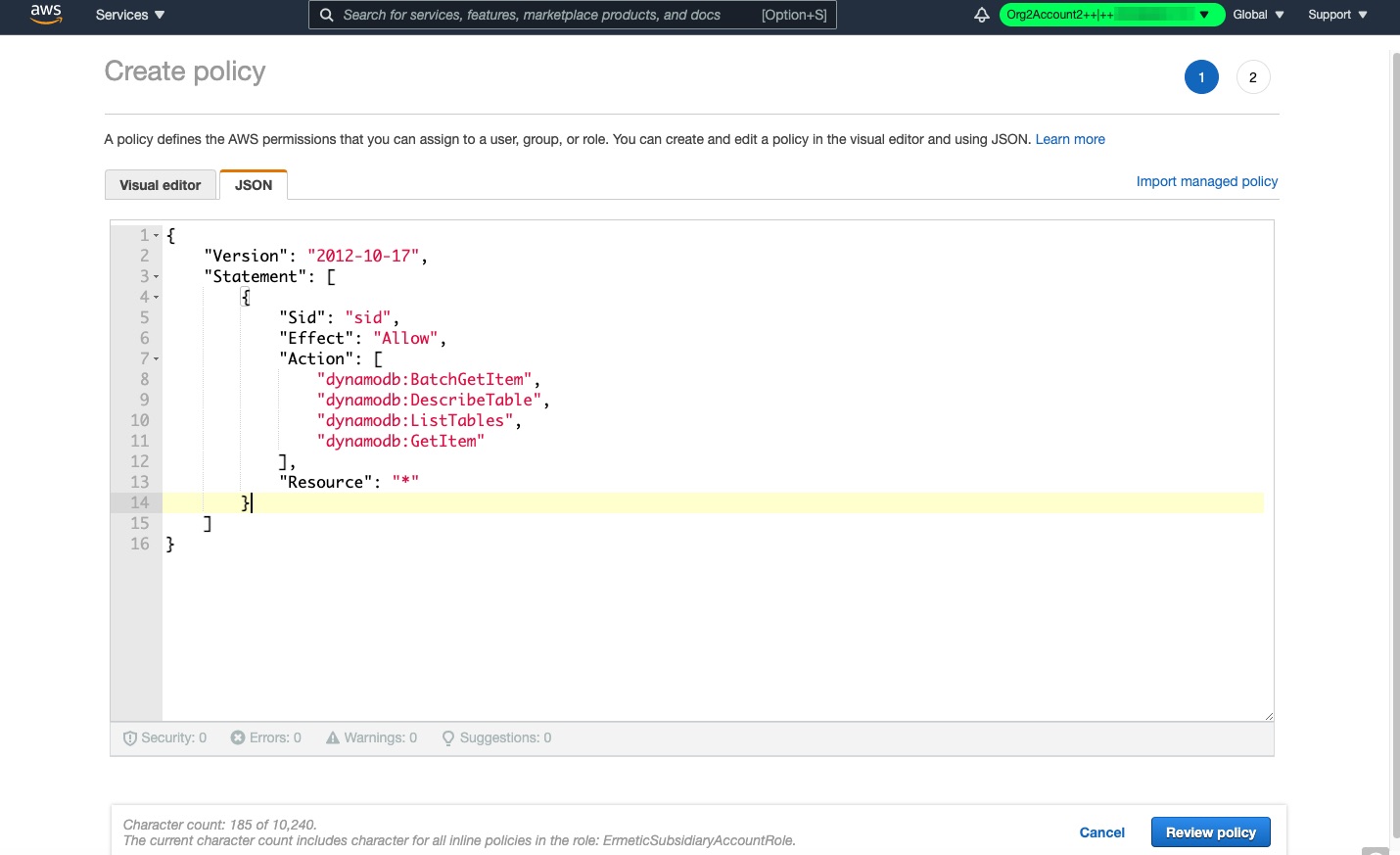
In the interest of not disrupting work, it may be tempting to not configure permissions at too fine-grained a level. Even if you wanted to verify if permissions are excessive, trying to weave through cloud complexity to figure it out would take you too much time. For example, AWS provides a complex evaluation process for determining if an identity can access certain resources; the tree requires practitioners to weed through the many components at play beyond the policy attached to the identity, including resource-based policies, permission boundaries, SCPs and even session policies. And that doesn’t even cover the fact that, in the case of AWS, identities can assume roles and therefore acquire even more permissions. In short, determining least privilege requires extensive, granular analysis within an environment.
Some compliance requirements do provide specific instructions regarding least privilege. For example, the CIS benchmark has an article that prohibits the use of any policy that provides administrative privileges. In the case of the example above, this would require removing the use of the wildcard on the actions of resources.
However, other compliance articles are more vague when describing least privilege requirements, leaving practitioners to try to figure out how to correctly define and implement the relevant policies. Where is a cloud security professional to even start?
Is CSPM (Cloud Security Posture Management) the Solution for Compliance Management?
To meet compliance requirements and challenges, and allow for easier compliance management, many companies use Cloud Security Posture Management (CSPM). CSPM tools automatically monitor risks in cloud configurations and settings, and map them to security standards; some offer remediation. CSPM tools, then, simplify the compliance process for cloud security professionals and help enhance security for the entire organization. They offer a good starting point (albeit not a complete solution) for compliance and cloud security.
To discover more, read our post what is CSPM.
The Benefits of Compliance Monitoring Using CSPM
CSPM tools offer multiple benefits for cloud security teams that use them. These include:
Technologically Specific
CSPMs help organizations ensure their specific cloud applications and services are compliant. This capability transforms the abstract compliance standards and makes them specific to an organization’s exact cloud configurations. A CSPM will review network data storage, API settings, configuration data, and more; compare and correlate with standards like GDPR, PCI, CIS, and others; and determine which nuts and bolts need to be rescrewed and how to comply with them.
Visibility: Cloud Compliance Monitoring and Reporting
CSPM tools typically provide visibility into all the cloud assets that make up the configurations, workloads and services. Such visibility empowers security professionals to better understand their organization’s cloud infrastructure and, as a result, take more control and ownership of it when modifying security controls.
A good CSPM tool will provide a compliance dashboard with understandable compliance reporting, which can also be downloaded as PDFs and shared with other stakeholders as well as auditors to show and prove compliance.
Anomaly Detection
One of the challenges of cloud security professionals is to go through all the compliance articles, understand their language and meaning, translating the compliance language to their cloud computing platform or infrastructure, and identify gaps.
Luckily, CSPM tools do this for them. By mapping an organization’s cloud configurations to the instructions in the standards, CSPM tools detect anomalies so they can be fixed (and some tools even automatically remediate them).
Evaluation & Recommendations
CSPM tools don’t just pull up a list of compliance gaps. Some CSPM solutions evaluate and prioritize them, and might even recommend the best way to mitigate them by suggesting remediative policies. This intelligent process helps security professionals ensure there are no misunderstandings or manual errors during cloud security setup and configuration, which could lead to a compliance breach (and an attacker breach).
Compliance Enforcement
By creating a solution for understanding and monitoring compliance, CSPM tools de facto enforce compliance. Circling back to the reasons described above for getting cloud compliant, this helps organizations abide by legal requirements, answer business needs and enhance their security. As a by-product, CSPM tools also help achieve continuous compliance.
Quick Implementation
CSPM tools are meant to relieve the workload, not add to it. Therefore, setting up should be easy and swift.

The Downside of CSPM Tools
CSPM tools might seem like the answer to ensuring cloud security but have their shortcomings. Being compliant does not necessarily mean being secure. There are some security capabilities that CSPMs do not perform, like identity management, applying security at the data or application layers, advanced workload protection and more.
What does this mean for cloud security? When looking at identity management, this means CSPM tools cannot support access and least privilege controls. Going back to our example of attempting to execute least privilege, CSPMs lack the granularity and context that security professionals need to understand the scope of permissions and entitlements for each identity.
This is because the tens of thousands of users and services in the cloud, which have access to thousands of resources, have made identity and entitlement management very hard to manage. Even a CSPM tool cannot achieve this on its own. As a result, when it comes to identity access management, a CSPM alone is not enough to achieve compliance and remediate vulnerabilities.
In addition, CSPM tools do not enable customization of how standards are enforced, reported, alerted on or remediated. When organizations create their own policies, they sometimes need to define how they are related to compliance standards. CSPM tools do not enable customizing policy compliance.
CSPM and CIEM: Better Together
CIEM tools are bespoke technologies for managing the entitlements of human and service identities in cloud computing services. They provide identification, visibility, reporting and remediation of risky entitlements, which can help organizations when trying to enforce compliance policies on identity management.
Therefore, the best solution for compliance and least privilege is a cloud infrastructure security platform that includes best of breed CIEM and robust CSPM. Read more information about what CIEM is.
Today, many cloud providers are positioning themselves as CNAPP (cloud native application protection platform). This means they are consolidating multiple cloud security capabilities, including CSPM and CNAPP. But according to Gartner, this is still a hypothetical category. So while you’re preparing for CNAPP, choose a tool that protects your cloud infrastructure today.
To see the webinar this blog post is based on, which also includes a demo of a CSPM tool that provides compliance with the advantage of identity-based visibility and risk detection, click here.





