

Osterman Research: State of Cloud Security Maturity Report
Find out how more than 300 diverse organizations fared in assessing their cloud security maturity based on the Tenable Cloud Security model – and the implications and next steps.
It’s a new beginning! Ermetic is now Tenable Cloud Security.
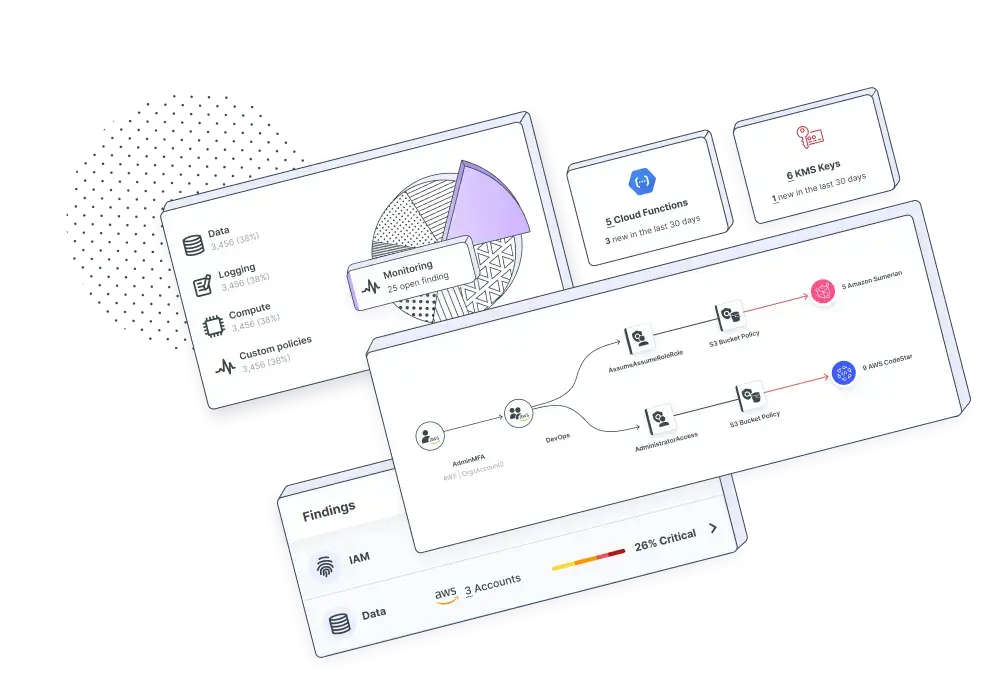
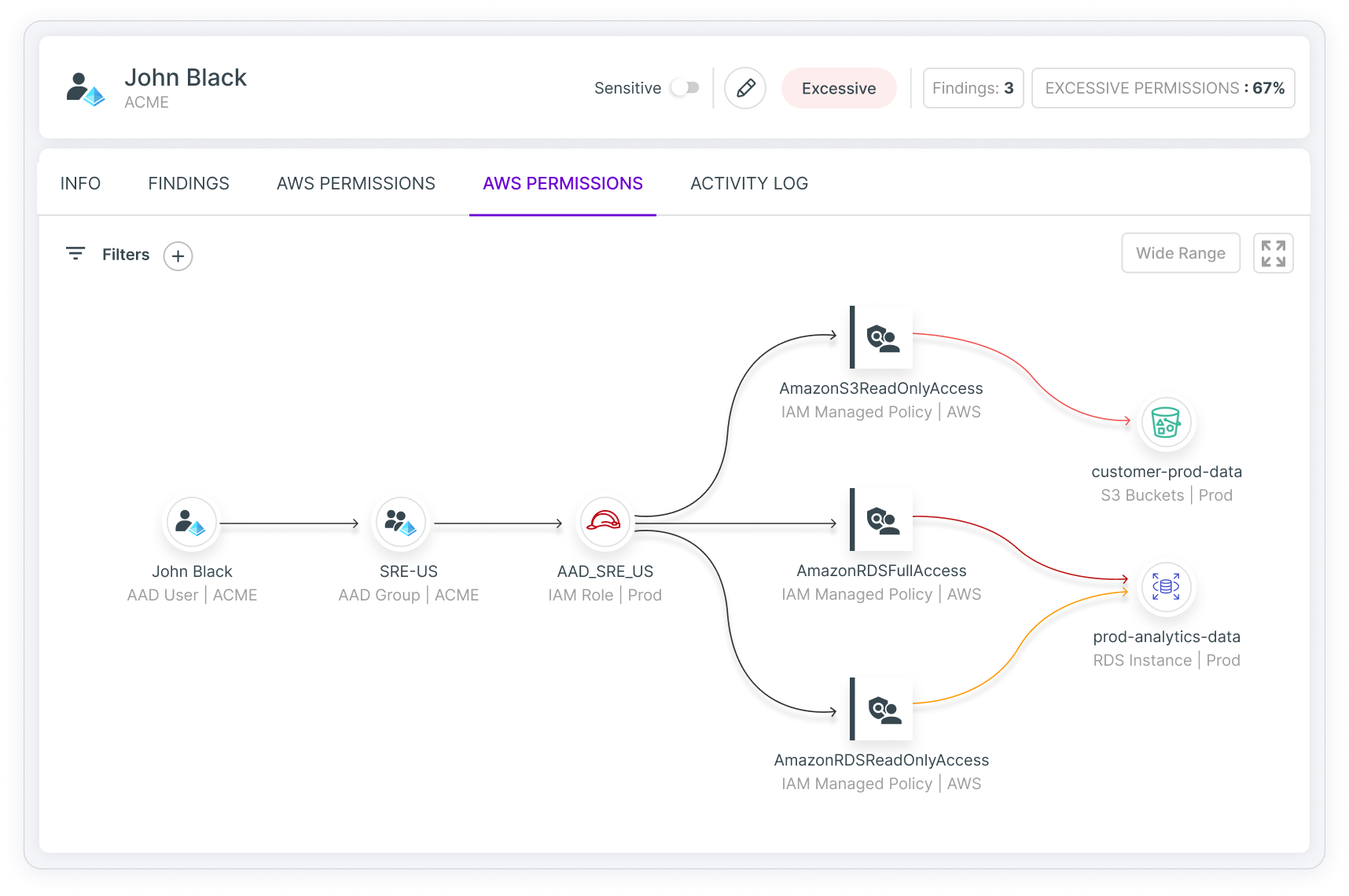
Govern human and machine identities with full multicloud visibility into access risks including overprivileged and unused entitlements, toxic combinations and privilege escalation.
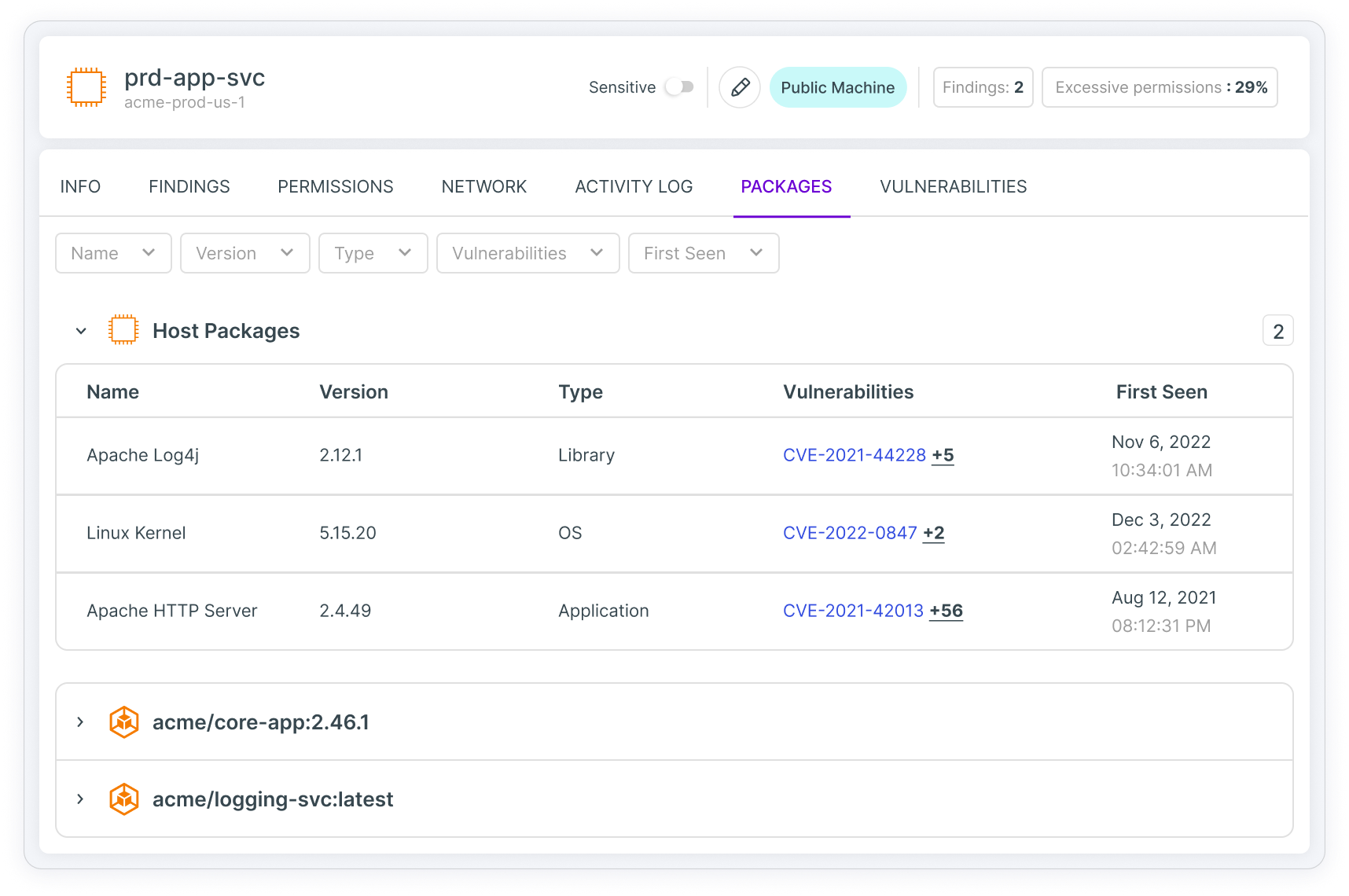
Continuously scan, detect and visualize most critical risks in workloads, including vulnerabilities, sensitive data, malware and misconfigurations across virtual machines, containers and serverless functions.
Detect and remediate misconfigurations, and comply with industry standards and best practice frameworks. Define and enforce custom policies for cloud configuration and IAM.
Reveal, prioritize and remediate security gaps and automate compliance for Kubernetes clusters across your cloud infrastructure. Unify visibility into K8s container configurations and empower stakeholders with steps for mitigating misconfigurations.
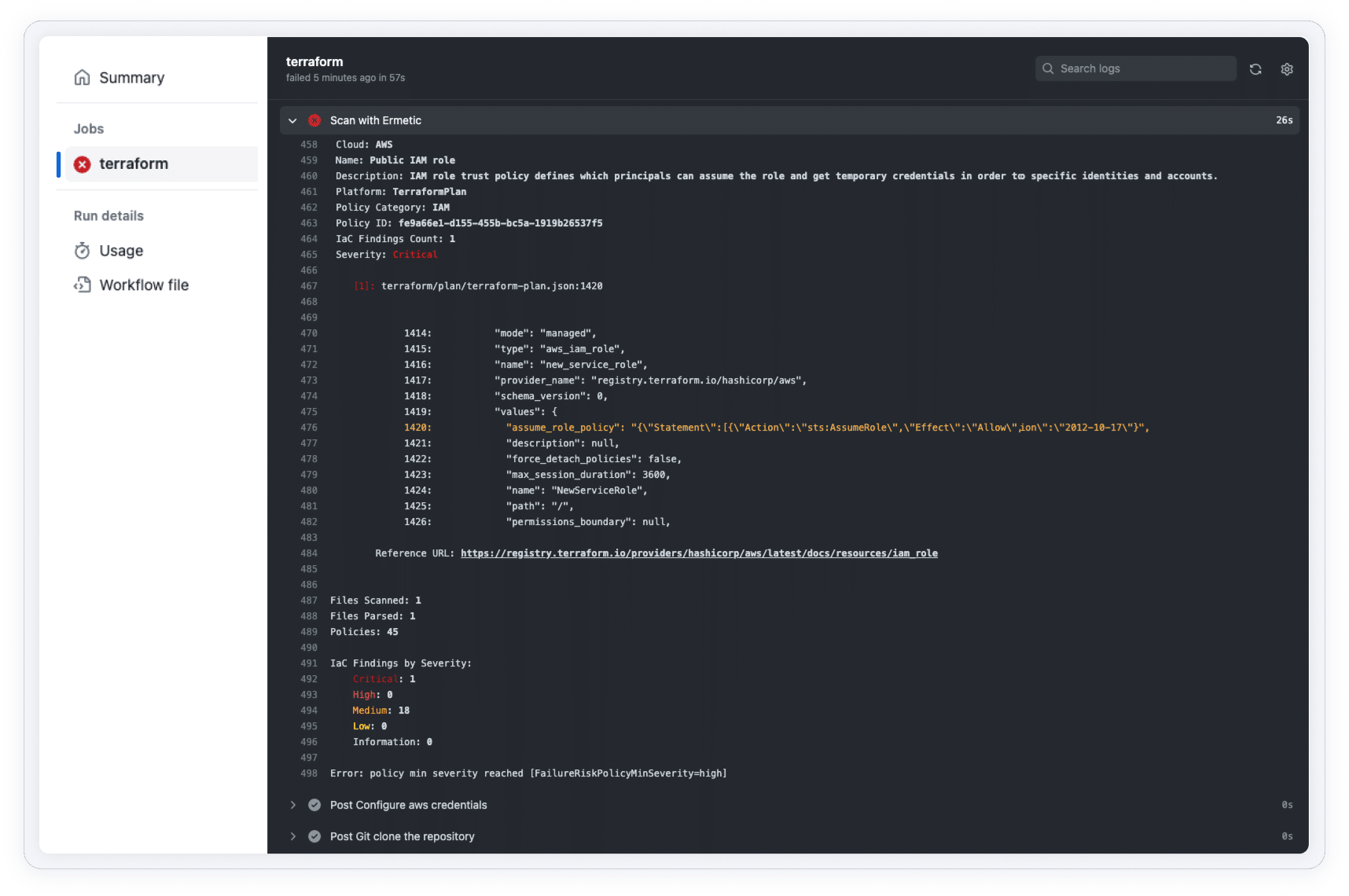
Implement shift-left security by scanning, detecting and fixing flaws in infrastructure as code. Reveal and remediate prioritized cloud risks in context and notify teams via integrations with ticketing and collaboration tools
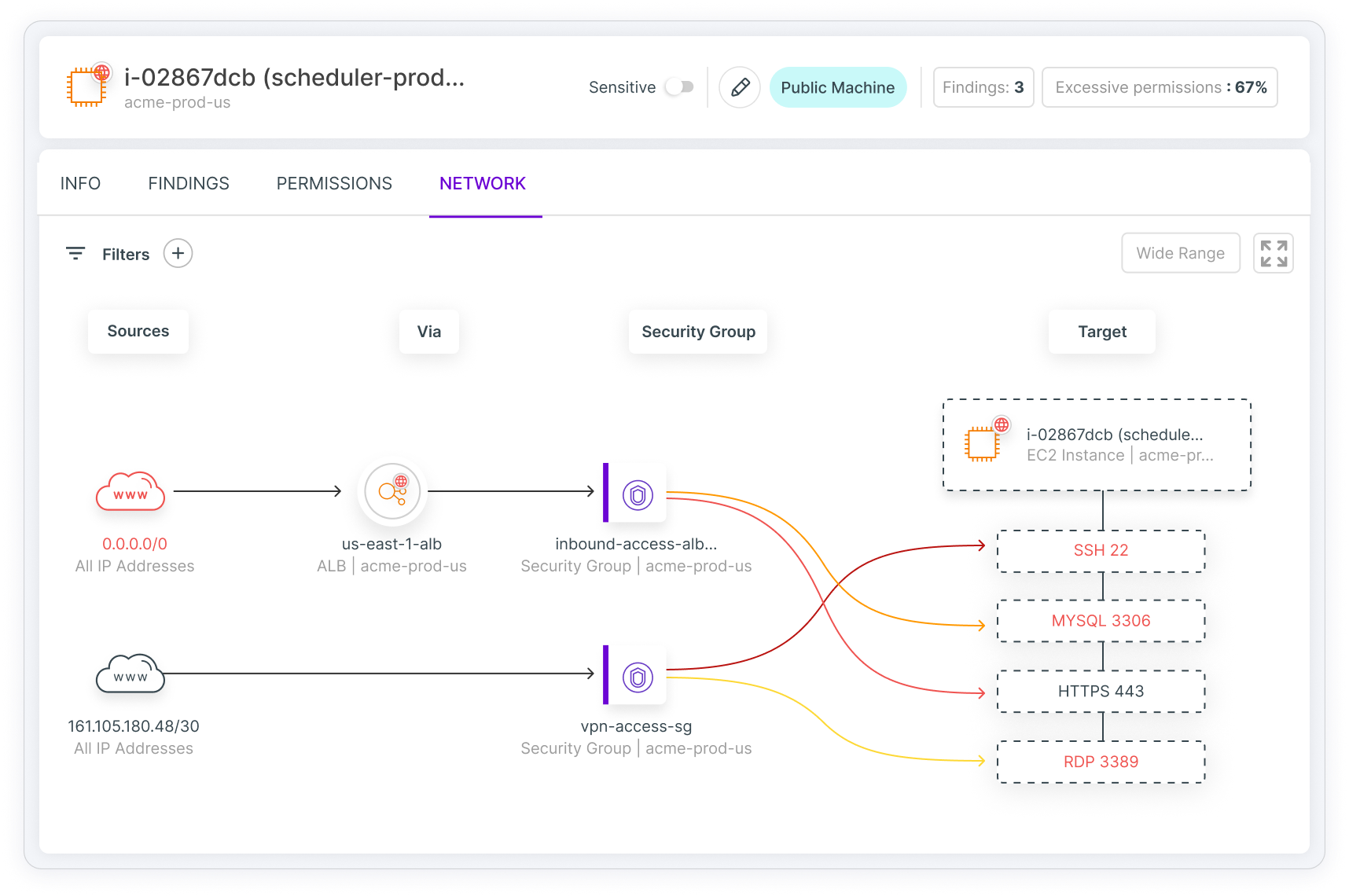
Reveal and visualize resources that are exposed to public access due to network misconfiguration. Find out who (or what) has network access to a resource and limit the access as much as possible.

Get speedy approval for as-needed, time-limited access and avoid non-revoked long-standing privileges, reducing the cloud attack surface. Enforce fine-grained least privilege policies to minimize risk while addressing the needs of the business.
To limit your largest attack surface and potential blast radius, you need to go deep on identities. Tenable Cloud Security helps organizations secure all their cloud entitlements, remove excessive permissions and detect suspicious behavior.
Using Ermetic [now Tenable Cloud Security] we removed all overprivileged configurations for IAM users and then for services; we did all the automatic remediation we could, and in two months, it didn’t break anything so we continued the momentum, working down the list, eliminating more risks.
Larry Viviano, Director of Information Security, IntelyCareErmetic [now Tenable Cloud Security] stood out. It was hitting every area of IAM that I knew was important. We were able to, in a short period of time, remediate hundreds of findings that we otherwise wouldn't have known existed.
David Christensen, Senior Information Security Executive & Cloud Security EvangelistErmetic [now Tenable Cloud Security] gives us overall transparency and deep, unified insight into our cloud architecture across both Azure and AWS, into the accounts of multiple tenants, subscriptions and whatever is in their identities.
Andreas Pfau, Tribe Lead Business Solutions, BilfingerErmetic [now Tenable Cloud Security] goes beyond permissions visibility to reveal IAM risk context that informs our busy devops team, facilitating their efforts in mitigating risk and minimizing disruption.
Guy Reiner, Co-founder and VP of R&D, Aidoc

Find out how more than 300 diverse organizations fared in assessing their cloud security maturity based on the Tenable Cloud Security model – and the implications and next steps.
All about CNAPPgoat, our open-source project designed to modularly provision vulnerable-by-design components in cloud environments.
By Lior Zatlavi
By default, compute instances in GCP are prone to a toxic combination that you should be aware of, and can…
By Lior Zatlavi

Watch Lior Zatlavi and Liv Matan's fwd:cloudsec 2023 session
By Tenable Cloud Security

Learn how an AWS service usage and permissions combination discovered by Ermetic [now Tenable Cloud Security] may increase risk upon…
By Tenable Cloud Security

Watch the presentation by Ermetic Research Lead Noam Dahan at fwd:cloudsec 2023
By Tenable Cloud Security
